Phishing emails have existed as long as email itself. These types of cyber attacks carry a huge risk to businesses large and small. According to SCORE.org 43% of cyberattacks targeted small businesses last year. In this post we lay out the possible dangers to your company and then provide a step-by-step guide to what to look out for.
How many emails have you had in the last week? 20? 100? 1000? How many of them were spam email? On the surface most spam emails (if they get through your spam filter) seem harmless, almost a little pathetic.
Looking through my junk folder this morning I can see the usual topics. 'Grow your business today', 'Free Website Audit', 'Guarantee Top of the Google! [sic]' and many more that are a little too rude to list here.
Look familiar? My Junk Email Folder this morning.
It's obvious to most people that these are unsolicited spam emails and, in most cases, if they even get read, they are simply deleted. However, among these easy to spot spam messages there are a far more dangerous kind. These are emails designed to trick you into performing an action such as installing unwanted software or sharing information you had no intention of sharing. They are created and sent by organised cybercriminals some of which can earn up to £2 million a year according to security firm Bromium.
Examples include:
Ransomware
Email is still the most common method for infecting computers with ransomware. The emails will try and trick you into installing software by clicking a link or opening an attachment. Once installed it encrypts your entire hard drive and demands a ransom to unencrypt. As these are criminal there is no guarantee that even following the instructions to the letter will result in your data being restored.
Phishing emails
A phishing scam is the dishonest attempt to get sensitive information from a user such as passwords, credit card number and banking details or other personal information though electronic communication. A play on the word fishing its exact origin is unclear. The strange spelling comes from hacker slang which tended to replace the letter f with ph. A famous example of this is the term phreaking which refers to the manipulation of telephone call routing.
Spear phishing
This is a more targeted version of the phishing attempts above. The target could be an individual or a specific company. The scammers conduct research on the target to make the emails seem far more legitimate to the target than the average scam email. They could include name dropping colleagues, mentioning clients and even various day-to-day internal business. All to add background and increase the chances of the email fooling the target.
Whaling
This is like spear phishing above but is even more targeted. In this type of scam, the criminals will target specific high-profile business executives such as the managing director or CEO. Large amounts of research is done and in some cases fake website are created for use in the narrative of the attack. The nature of this strategy means it likely only targets a few individuals making it harder for the system administrators to spot.
Key loggers
These are applications that record the keystrokes made on a computer. They can be delivered via email as an attachment or installed when a link is clicked. The data captured can then be processed by cybercriminals to extract passwords and other personal information. Key loggers are the reason many banking systems offer the option to use a mouse operated on-screen keyboard as this makes them unable to 'see' what you are typing.
Social engineering
This is a catch-all term to describe tactics designed to manipulate a target though human interaction. The goal could be to gain passwords or other sensitive information, bank account details, credit card numbers and even to perform identity theft. These scams often target very human traits such as greed, curiosity or the fear of public embarrassment. A well-known example is the Advance-fee scam (also known as the Nigeria Scam) which can actually be traced back to the late 19th century confidence trick The Spanish Prisoner.
If all the above examples, came in the easy to spot emails we talked about at the start then our computers would all be a lot safer. However, it’s fair to say that with the increased danger of the payload or intent of the scam email come an increase in the sophistication employed by cyber criminals to trick you into thinking it's a genuine email.
Here are the main things you should be keeping an eye on when dealing with all and any emails to avoid becoming the victim of a scam or phishing campaign.
Check the sender
- Is the email from someone you usually have dealings with? Make sure to check both the name and the email address. If you have suspicions double check the persons details in your contacts.
- Is it from someone you've not heard from for a while? Or at least not heard from using that email address for a while. This could be a sign that an old unattended mailbox has been compromised and the owner is unaware (or no longer cares).
- Is it from a public email service? No respectable company will contact you using a service such as Gmail or Yahoo! Mail. There are also countless free email providers that might not be so familiar with such as GMX, Yandex and Fastmail. It's always worth checking domain the email seems to come from if something feels not quite right.
- Even if the email is from someone you know or have regular dealings with does it seem out of character or just generally a bit strange (is the greeting overly familiar or not familiar enough for example). This could be a sign that their mailbox has been hacked or compromised in some way.
- Are you sure the email address is what it seems? Criminals often use emails on domains that are similar to the legitimate sites of trusted companies or brands. If in doubt a quick google of the email address could flag potential risks.
- Spoofed email addresses: It is technically possible for spammers to make an email address appear to come from a different email address than it really did. Due to advances in security this is far less common that it once was. Certainly, no respectable company that sends out emails to its customers would do so without spoofing protection. Also always keep in mind that these companies would never ask for your password or other confidential information in an unsolicited email.
Check the recipients
- A common tactic in phishing messages is to make it seem that you have been accidentally copied in on an email between two other parties. The email could have an attachment or link that you could be tempted to click or open out of curiosity.
- If there are other recipients within your organisation check them thoroughly. Do they seem like a strange mixture? Perhaps people from wildly different departments or even email addresses of people that no longer work for the company. Both could be clues that the email is fraudulent.
Check the subject line
- Does the email appear to be a reply to something that you didn't send? This is something we are seeing more and more. The simple inclusion of RE: at the start of the subject lines is supposed to trick the user into thinking it's a reply to something they initially sent and just don't remember. This could possible encourage you to be less suspicious and too hasty in trying to deal with it.
- Does the subject line contain spelling errors or bad grammar? Especially when compared to previous emails you may have had from this sender or the professionalism of communication you would expect from a well-known company or brand.
Check the content
- Is the branding consistent with who the email claims to come from? Many scam emails will pretend to come from companies or brands you will likely be familiar with. The scammers are banking on this to fool you into a false sense of security. If there is a signature check the quality of the logo and that the general presentation is up to scratch.
- As with the subject line thoroughly check the email for spelling, grammatical errors and odd use of language. It's interesting to note that in some cases it has been suggested that these types of errors are purposeful and help the scammers by filtering out those not so easily tricked.
- Some scam emails contain outright threats based on claiming to have incriminating information, text messages or even images of you in compromising situations. These should all be ignored. Most will demand money (like ransomware) but some will use the threat to scare you into click the link or opening an attachment.
- Like the above but less frightening are scam emails that are designed to be mistaken for notifications from social media sites such as Facebook. Typically, they hint at something you could be interested in such as a friend sending you a message, or someone commented on one of your photos. More than likely clicking the link will start an attempt to install malicious software on your computer or device.
- Does the email appear to come from a well-known company and ask you to reset your password or update your details? This is another common tactic. The companies used range from banks and credit card companies right through to streaming services such as Netflix. It's important to realise that these companies would never contact you in this manner. At most you could receive an email when your account is accessed from a device that their system is unfamiliar with. If you are worried an account may have been compromised the best thing to do would be to open a browser and login to the account and change the password there. Never, ever click a link in an email to do this.
- Does the email contain an offer or claim you have won a prize that seems too good to be true? Common sense should tell you that these are a scam. Especially if it's a prize for a contest you didn't even enter.
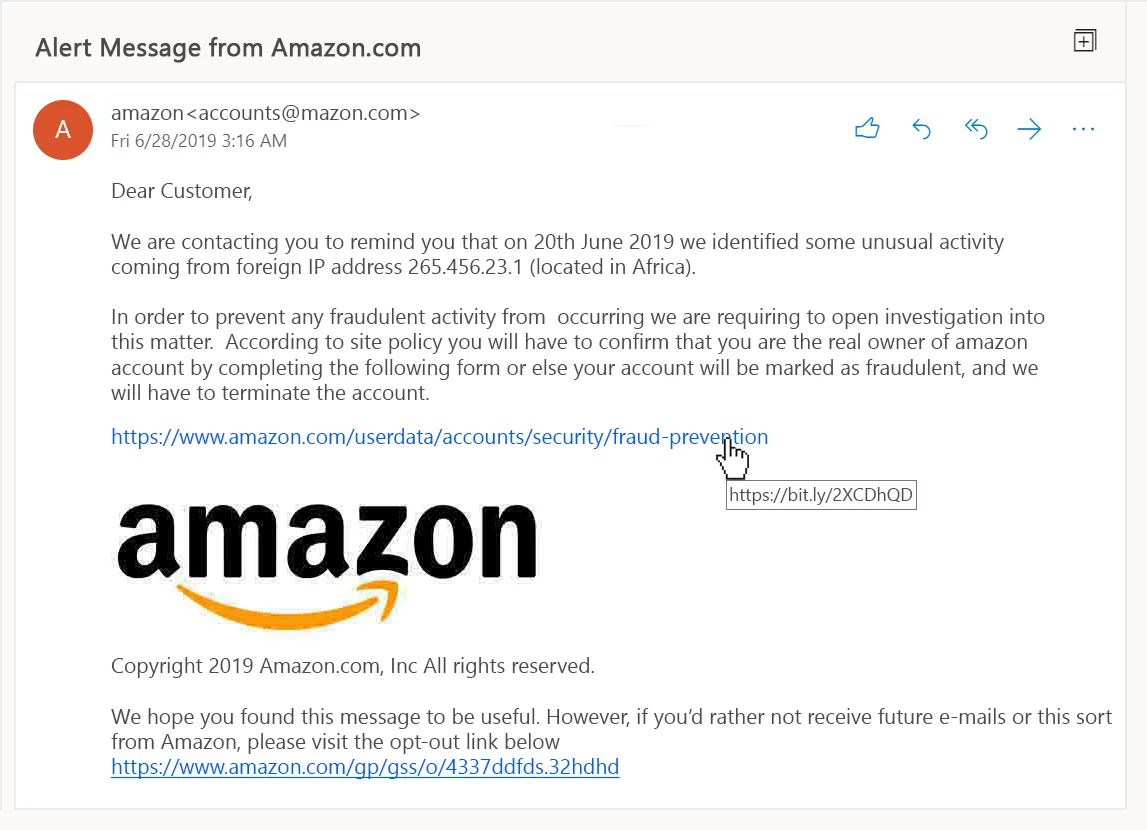
An example of a phishing email pretending to be from Amazon. If you look closely there are many issues with it. There are at least 6 clear warnings and another few that could be considered red flags. Can you spot them all? Answer in the comments.
Check the attachments
- If an email comes with an attachment, it's important to identify its purpose. Is it referenced in the email or is its presence unexpected? If the attachment seems strange, we would recommend not opening it. If you know the sender, you could contact them and request further information.
- Always Scan! Almost all files types have the potential to be malicious. PDFs, Word docs and even image files can all contain malware. Security firm F-Secure claims 85% of malicious emails have a .DOC, .XLS, .PDF, .ZIP, or .7Z attached. You should always scan attachments even if you know the sender. Their systems may have been infected without their knowledge.
Check the links
- Check any links in an email before you click them. It's simple for scammers to mask links so they say one thing but actually link to something else. You can check them by hovering your mouse over each one. A tool tip should popup displaying the links true destination. Any difference could indicate that it is fraudulent. The difference can be tiny so it's worth double checking. www.nationalwestministerbank.com vs www.natoinalwestminsterbank.com for example.
- Some scam emails dispense with any attempt at subterfuge and just contain a link. The thinking is that any 'framing' could dissuade potential victims from clicking it. Giving them as little to go on as possible could increase click rates in some cases.
This may look like an awful lot of things to check each time you receive a message but much of it is common sense. The normal day-to-day dealings you have with your colleagues and clients will also alert you to anything that feels odd. Security systems can also help by scanning emails and attachments before they even hit your inbox. This is exactly what we use internally and have also helped many of our clients set up.
If you would like to discuss how such systems can help reduce the risk to your company and employees call us on 01293 562 700 for an informal chat about the options. Alternatively send us a message online or arrange for us to call you back at a time that suits you.
Designer
Mike is a designer at Optima Systems. He grew up in West London and now lives by the sea. His first love was music which led to jobs in recording engineering and a number of years as a front of house sound engineer and theatre stage manager. Having been taught the basics of HTML while at university he continued to develop websites as a hobby. It wasn't long before he realised the hobby was the more rewarding pursuit. More about Mike.
Ask Mike about Software Solutions / Website Design and Development
- Cyber Security Solutions for Business
- Can Windows Defender be trusted to look after your PC security?
- Cryptolocker – Infection removal Updated
- How to delete your social media profiles – and why you probably should
- Server Support for Businesses
- Our experience moving to Microsoft Office 365
- New password scam sends victims old passwords, attempts to blackmail for ‘viewing adult content’
- Check if any of your online ‘identities’ have been compromised with Hack Notice
- New voluntary code for the Banks to repay victims of push payment scam

